Get the best Cisco ICND1 100-105 dumps pdf and vce practice files from leads4pass, offer the latest Cisco ICND1 100-105 dumps exam training materials and study guides. https://www.leads4pass.com/100-105.html dumps pdf practice materials free update. Latest Cisco ICND1 100-105 dumps exam questions and answers download free try, pass Cisco 100-105 exam test easily.
Download free latest Cisco 100-105 dumps PDF from google drive: https://drive.google.com/open?id=0B_7qiYkH83VReEJYRlhNVjdGeVU
Download free latest Cisco 210-065 dumps PDF from google drive: https://drive.google.com/open?id=0B_7qiYkH83VRODRqVmVBYWxuc0k
QUESTION 1
Some routers have been configured with default routes. What are some of the advantages of using default routes? (Choose two)
A. They establish routes that will never go down.
B. They keep routing tables small.
C. They require a great deal of CPU power.
D. They allow connectivity to remote networks that are not in the routing table
E. They direct traffic from the internet into corporate networks.
Correct Answer: BD
QUESTION 2
Which two of these statements are true of IPv6 address representation? (Choose two.)
A. There are four types of IPv6 addresses: unicast, multicast, anycast, and broadcast.
B. A single interface may be assigned multiple IPv6 addresses of any type.
C. Every IPv6 interface contains at least one loopback address.
D. The first 64 bits represent the dynamically created interface ID.
E. Leading zeros in an IPv6 16 bit hexadecimal field are mandatory.
Correct Answer: BC
QUESTION 3
If a host experiences intermittent issues that relate to congestion within a network while remaining connected, 100-105 dumps what could cause congestion on this LAN?
A. half-duplex operation
B. broadcast storms
C. network segmentation
D. multicasting
Correct Answer: B
QUESTION 4
Refer to the exhibit.
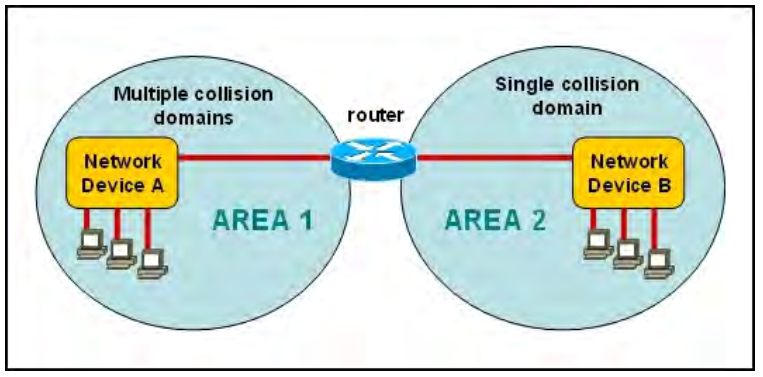
A network has been planned as shown. Which three statements accurately describe the areas and devices in the network plan? (Choose three.)
A. Network Device A is a switch.
B. Network Device B is a switch.
C. Network Device A is a hub.
D. Network Device B is a hub.
E. Area 1 contains a Layer 2 device.
F. Area 2 contains a Layer 2 device.
Correct Answer: A,D,E
QUESTION 5
What is one requirement for interfaces to run IPv6? 100-105 dumps
A. An IPv6 address must be configured on the interface.
B. An IPv4 address must be configured.
C. Stateless autoconfiguration must be enabled after enabling IPv6 on the interface.
D. IPv6 must be enabled with the ipv6 enable command in global configuration mode.
Correct Answer: A
QUESTION 6
Which statements accurately describe CDP? (Choose three.)
A. CDP is an IEEE standard protocol.
B. CDP is a Cisco proprietary protocol.
C. CDP is a datalink layer protocol.
D. CDP is a network layer protocol.
E. CDP can discover directly connected neighboring Cisco devices.
F. CDP can discover Cisco devices that are not directly connected.
Correct Answer: B,C,E
QUESTION 7
Which statements are true regarding ICMP packets? 100-105 pdf (Choose two.)
A. They acknowledge receipt of TCP segments.
B. They guarantee datagram delivery.
C. TRACERT uses ICMP packets.
D. They are encapsulated within IP datagrams.
E. They are encapsulated within UDP datagrams.
Correct Answer: CD
QUESTION 8
Which of the following statements are TRUE regarding Cisco access lists? (Choose two.)
A. In an inbound access list, packets are filtered as they enter an interface.
B. In an inbound access list, packets are filtered before they exit an interface.
C. Extended access lists are used to filter protocol-specific packets.
D. You must specify a deny statement at the end of each access list to filter unwanted traffic.
E. When a line is added to an existing access list, it is inserted at the beginning of the access list.
Correct Answer: AC
QUESTION 9
Which layer of the TCP/IP stack combines the OSI model physical and data link layers?
A. Internet layer
B. transport layer
C. application layer
D. network access layer
Correct Answer: D
QUESTION 10
What are two recommended ways of protecting network device configuration files from outside network security threats? (Choose two.) 100-105 dumps
A. Allow unrestricted access to the console or VTY ports.
B. Use a firewall to restrict access from the outside to the network devices.
C. Always use Telnet to access the device command line because its data is automatically encrypted.
D. Use SSH or another encrypted and authenticated transport to access device configurations.
E. Prevent the loss of passwords by disabling password encryption.
Correct Answer: BD
Read more: https://www.leads4pass.com/100-105.html dumps pdf questions and answers free update.
Watch the video to learn more:

