
Fully updated CCNP 350-701 dumps in March 2023, including 598 latest exam questions and answers, verified by the leads4pass CCNP team, true and effective. And provide 15 latest free CCNP 350-701 exam questions online practice tests.
Download CCNP 350-701 dumps: https://www.leads4pass.com/350-701.html, choose to use PDF files to read and study, or VCE simulation engine to assist exercises, to help candidates easily cope with the 350-701 SCOR certification exam.
CCNP 350-701 Dumps Exam Questions Online Practice Test:
| Type | Number of exam questions | Exam name | Exam code | Answers |
| Free | 15 | Implementing and Operating Cisco Security Core Technologies (SCOR) | 350-701 | Check |
Question 1:
What are two benefits of Flexible NetFlow records? (Choose two)
A. They allow the user to configure flow information to perform customized traffic identification
B. They provide attack prevention by dropping the traffic
C. They provide accounting and billing enhancements
D. They converge multiple accounting technologies into one accounting mechanism
E. They provide monitoring of a wider range of IP packet information from Layer 2 to 4
Reference:
https://www.cisco.com/en/US/docs/ios/fnetflow/configuration/guide/cust_fnflow_rec_mon_e xternal_docbase_0900e4b18055d0d2_4container_external_docbase_0900e4b181b413 d9.html#wp1057997Note: Traditional NetFlow allows us to monitor from Layer 2 to 4 but Flexible NetFlow goes beyond these layers.
Question 2:
What is a description of micro-segmentation?
A. Environments apply a zero-trust model and specify how applications on different servers or containers can communicate
B. Environments deploy a container orchestration platform, such as Kubernetes, to manage the application delivery
C. Environments implement private VLAN segmentation to group servers with similar applications.
D. Environments deploy centrally managed host-based firewall rules on each server or container
Question 3:
A user has a device in the network that is receiving too many connection requests from multiple machines. Which type of attack is the device undergoing?
A. phishing
B. slow loris
C. pharming
D. SYN flood
Question 4:
What are the two characteristics of Cisco DNA Center APIs? (Choose two)
A. Postman is required to utilize Cisco DNA Center API calls.
B. They do not support Python scripts.
C. They are Cisco proprietary.
D. They quickly provision new devices.
E. They view the overall health of the network
Question 5:
Refer to the exhibit.
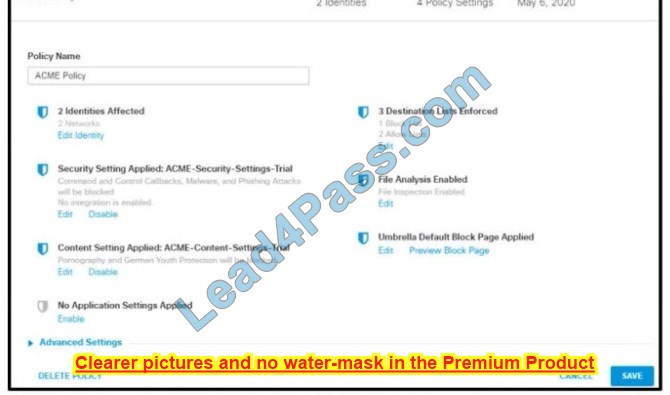
How does Cisco Umbrella manage traffic that is directed toward risky domains?
A. Traffic is proxied through the intelligent proxy.
B. Traffic is managed by the security settings and blocked.
C. Traffic is managed by the application settings, unhandled and allowed.
D. Traffic is allowed but logged.
Question 6:
What is the function of SDN southbound API protocols?
A. to allow for the dynamic configuration of control plane applications
B. to enable the controller to make changes
C. to enable the controller to use REST
D. to allow for the static configuration of control plane applications
Reference: https://www.ciscopress.com/articles/article.asp?p=3004581andseqNum=2 Note: Southbound APIs help us communicate with data plane (not control plane) applications
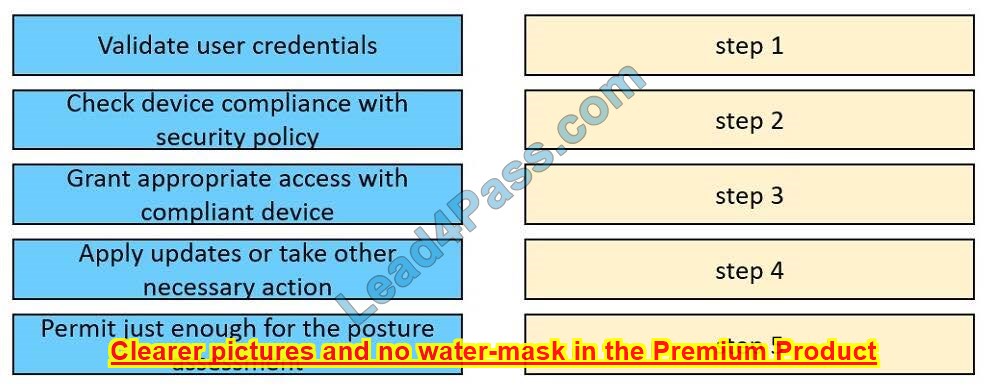
Question 7:
DRAG DROP
Drag and drop the posture assessment flow actions from the left into a sequence on the right.
Select and Place:
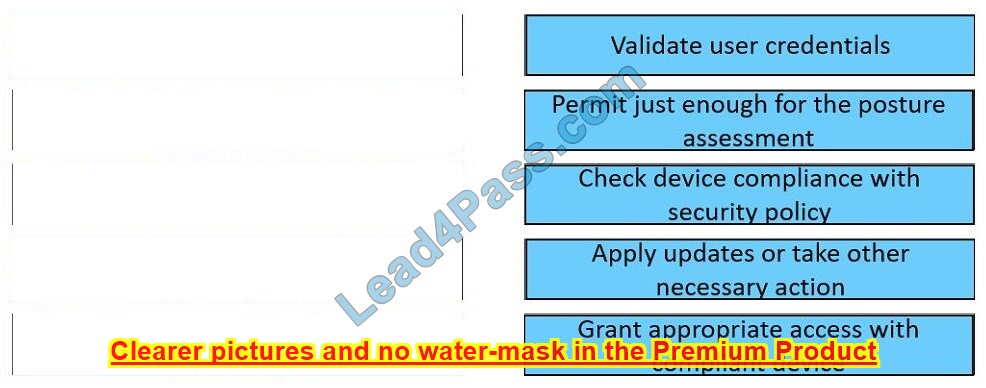
Correct Answer:
Question 8:
What is the primary role of the Cisco Email Security Appliance?
A. Mail Submission Agent
B. Mail Transfer Agent
C. Mail Delivery Agent
D. Mail User Agent
Question 9:
A switch with Dynamic ARP Inspection enabled has received a spoofed ARP response on a trusted interface. How does the switch behave in this situation?
A. It forwards the packet after validation by using the MAC Binding Table.
B. It drops the packet after validation by using the IP and MAC Binding Table.
C. It forwards the packet without validation.
D. It drops the packet without validation.
Question 10:
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two)
A. accounting
B. assurance
C. automation
D. authentication
E. encryption
Question 11:
An organization has DHCP servers set up to allocate IP addresses to clients on the LAN.
What must be done to ensure the LAN switches prevent malicious DHCP traffic while also distributing IP addresses to the correct endpoints?
A. Configure Dynamic ARP Inspection and add entries in the DHCP snooping database
B. Configure DHCP snooping and set an untrusted interface for all clients
C. Configure Dynamic ARP Inspection and antispoofing ACLs in the DHCP snooping database
D. Configure DHCP snooping and set a trusted interface for the DHCP server
Question 12:
DRAG DROP
Drag and drop the capabilities of Cisco Firepower versus Cisco AMP from the left into the appropriate category on the right.
Select and Place:
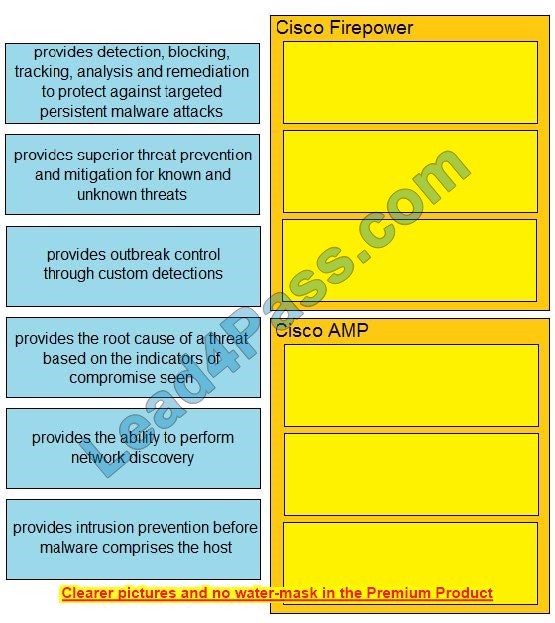
Correct Answer:
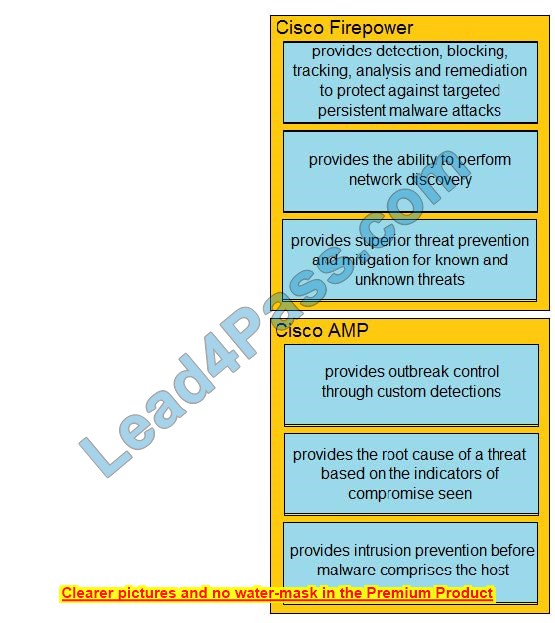
Description automatically generated with low confidence ExplanationThe Firepower System uses network discovery and identity policies to collect host, application, and user data for traffic on your network.
You can use certain types of discovery and identity data to build a comprehensive map of your network assets, perform forensic analysis, behavioral profiling, access control, and mitigate and respond to the vulnerabilities and exploits to which your organization is susceptible.
The Cisco Advanced Malware Protection (AMP) solution enables you to detect and block malware, continuously analyze for malware, and get retrospective alerts.
AMP for Networks delivers network-based advanced malware protection that goes beyond point-in-time detection to protect your organization across the entire attack continuum.
before, during, and after an attack. Designed for Cisco Firepower? network threat appliances, AMP for Networks detects, blocks, tracks, and contains malware threats across multiple threat vectors within a single system.
It also provides the visibility and control necessary to protect your organization against highly sophisticated, targeted, zero-day, and persistent advanced malware threats.
Question 13:
An administrator is establishing a new site-to-site VPN connection on a Cisco IOS router.
The organization needs to ensure that the ISAKMP key on the hub is used only for terminating traffic from the IP address 172.19.20.24. Which command on the hub will allow the administrator to accomplish this?
A. crypto ca identity 172.19.20.24
B. crypto isakmp key Cisco0123456789 172.19.20.24
C. crypto enrollment peer address 172.19.20.24
D. crypto isakmp identity address 172.19.20.24
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/security/a1/sec-a1-cr- book/sec-crc4.html
#wp3880782430The command “crypto enrollment peer address” is not valid either. The command “crypto ca identity …” is only used to declare a trusted CA for the router and puts you in the identity configuration mode. Also, it should be followed by a name, not an IP address. For example: “crypto ca identity CA-Server” -> Answer A is not correct. Only answer B is the best choice left.
Question 14:
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
A. Smurf
B. distributed denial of service
C. cross-site scripting
D. rootkit exploit
Cross-site scripting (also known as XSS) occurs when a web application gathers malicious data from a user. The data is usually gathered in the form of a hyperlink that contains malicious content within it.
The user will most likely click on this link from another website, instant message, or simply just read a web board or email message. Usually, the attacker will encode the malicious portion of the link to the site in HEX (or other encoding methods) so the request is less suspicious looking to the user when clicked on.
For example, the code below is written in hex:
Click Here is equivalent to Click HereNote: In the format “and#xhhhh”, hhhh is the code point in hexadecimal form.
Question 15:
An engineer needs to detect and quarantine a file named abc424400664 zip based on the MD5 signature of the file using the Outbreak Control list feature within Cisco Advanced Malware Protection (AMP) for Endpoints The configured detection method must work on files of unknown disposition Which Outbreak Control list must be configured to provide this?
A. Blocked Application
B. Simple Custom Detection
C. Advanced Custom Detection
D. Android Custom Detection
…
Verify answer:
| Number | Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| Answers | AD | A | D | DE | B | B | IMAGE | B | C | BC | D | IMAGE | B | C | C |
Download 598 latest 350-701 SCOR certification exam questions: https://www.leads4pass.com/350-701.html (350-701 dumps), and practice each question carefully to ensure that you pass the exam 100% successfully.
Summarize:
The 350-701 SCOR certification exam is the Cisco CCNP Security core exam, so…
Help you prepare by practicing the leads4pass 350-701 dumps material, and help you successfully pass the 350-701 SCOR certification exam in the shortest time and the easiest way to learn.

