【2017 good news!】The best Cisco 400-251 dumps exam study materials online are written according to the latest real IT exams. https://www.leads4pass.com/400-251.html
【latest version】All the Cisco 400-251 dumps exam practice questions and answers are revised by the skillful experts in leads4pass.com. 100% success and guarantee to pass 400-251 exam test quickly and easily at first attempt.
QUESTION 1
What is the first step in performing a risk assessment?
A. Identifying critical services and network vulnerabilities and determining the potential impact of their compromise or failure.
B. Investigating reports of data theft or security breaches and assigning responsibility.
C. Terminating any employee believed to be responsible for compromising security.
D. Evaluating the effectiveness and appropriateness of the organization’s current risk-management activities.
E. Establishing a security team to perform forensic examinations of previous known attacks.
Answer: A
QUESTION 2
Which two statements about the MACsec security protocol are true? (choose two.)
A. Stations broadcast an MKA heartbeat that contains the key server priority
B. The SAK is secured by 128 bit AES-GCM by default
C. When switch-to-switch link security is configured in manual mode, the SAP operation mode must be set to GCM
D. MACsec is not supported in MDA mode.
E. MKA heartbeats are sent at a default interval of 3 seconds.
Answer: AB
QUESTION 3
Which two options are benefits of network summarization? (Choose two.)
A. It can summarize discontiguous IP addresses.
B. It can easily be added to existing networks
C. it can increase the convergence of the network
D. It reduces the number of routes
E. It prevents unnecessary routing updates at the summarization boundary if one of the routes in the summary is unstable.
Answer: DE
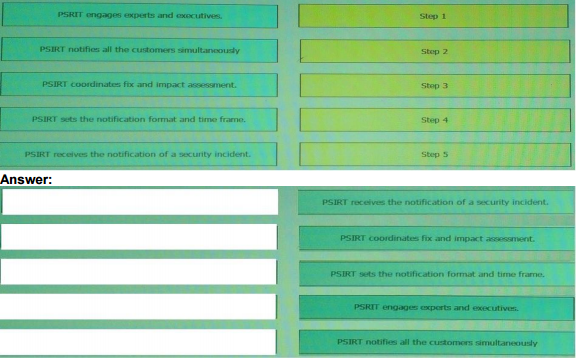
QUESTION 4
Which description of a virtual private cloud is true?
A. An on-demand configurable pool of shared software applications allocated within a public cloud environment, which provides tenant isolation
B. An on-demand configurable pool of shared data resources allocated within a private cloud environment, which provides assigned DMZ zones
C. An on-demand configurable pool of shared networking resources allocated within a private cloud environment, which provides tenant isolation
D. An on-demand configurable pool of shared computing resources allocated within a public cloud environment, which provides tenant isolation
Answer: D
QUESTION 5
Which two statements about SCEP are true? (Choose two) 400-251 dumps
A. CA servers must support GetCACaps response messages in order to implement extended functionality
B. The GetCRL exchange is signed and encrypted only in the response direction.
C. It is vulnerable to downgrade attacks on its cryptographic capabilities
D. The GetCert exchange is signed and encrypted only in the response direction.
E. The GetCACaps response message supports DES encryption and the SHA-128 hashing algorithm.
Answer: AC
QUESTION 6
Which effect of the ip nhrp map multicast dynamic command is true?
A. It configures a hub router to automatically add spoke routers to the multicast replication list of the hub
B. It enables a GRE tunnel to operate without the IPsec peer or crypto ACLs.
C. it enables a GRE tunnel to dynamically update the routing tables on the devices at each end of the tunnel
D. It configures a hub router to reflect the routes it learns from a spoke back to other spokes through the same interface
Answer: A
QUESTION 7
Which statement about VRF-aware GDOI group members is true?
A. IPsec is used only to secure data traffic.
B. The GM cannot route control traffic through the same VRF as data traffic
C. Multiple VRFs are used to separate control traffic and data traffic
D. Registration traffic and rekey traffic must operate on different VRFs
Answer: A
QUESTION 8
Which two statements about uRPF are true? (Choose two.)
A. The administrator can configure the allow-default command to force the routing table to use only the default route
B. It is not supported on the Cisco ASA security appliance.
C. The administrator can configure the ip verify unicast source reachable-via any command to enable the RPF check to work routing groups.
D. The administrator can use the show cef interface command to determine whether uRPF is enabled
E. In strict mode, only one routing path can be available to reach network devices on a subnet
Answer: DE
QUESTION 9 400-251 dumps
Which three statements about SXP are true? (Choose three )
A. It resides in the control plane, where connections can be initiated from a listener
B. Packets can be tagged with SGTs only with hardware support
C. Each VRF supports only one CTS-SXP connection
D. To enable an access device to use IP device tracking to learn source device IP addresses.
DHCP snooping must be configured.
E. The SGA ZBPF uses the SGT to apply forwarding decisions
F. Separate VRFs require different CTS-SXP peers, but they can use the same source IP addresses.
Answer: ABC
QUESTION 10
Which WEP configuration can be exploited by a weak IV attack?
A. When the static WEP password has been stored without encryption
B. When a per-packet WEP key is in use
C. When a 64-bit key is in use
D. When the static WEP password has been given away
E. When a 40-bit key is in use
F. When the same WEP key is used to create every pack
Answer: E
Read more: https://www.leads4pass.com/400-251.html 【100% Guaranteed Pass】
Watch the video to learn more:

