
Welcome to the updated guide for the Cisco 350-901 DEVCOR exam. This 2025 edition provides live updates on the Cisco Certified DevNet Professional certification, including PDF and VCE dumps with 365 days of free updates, online support, and cost-saving tips to help you prepare efficiently.
Obtain the latest valid 350-901 dumps: https://www.leads4pass.com/350-901.html (over 463 Q&A) from reliable providers like leads4pass or similar sources to ensure you’re studying the most current materials.
As of 2025, the exam is still in version 1.0, covering key topics in software development and APIs, but an upcoming update to v2.0 (renamed to “Designing, Deploying, and Managing Network Automation Systems – 350-901 AUTOCOR”) is set for February 3, 2026 – now is the perfect time to get started!
Download the free sample PDF here: [ https://drive.google.com/file/d/1T6IAexTvGJNRl65Lo3NC0hcSK4Dsky3z/view?usp=sharing ].
Take action now: Scroll down to explore the free sample questions and answers to test your knowledge and boost your confidence for the exam.
Cisco 350-901 Free Practice Questions and Answers
Updated 2025 – Here are 15 free Cisco 350-901 exam dumps to test your knowledge. Includes answers and explanations.
| Number of exam questions | Exam name | From | Release time |
| 15 | Developing Applications Using Cisco Core Platforms and APIs (DEVCOR) | Leads4pass | Sep, 2025 |
Question 1 (DRAG DROP)
Drag and drop the code snippets from the bottom onto the boxes where the code is missing to complete the API call to implement error handling. Not all options are used.
Select and Place:
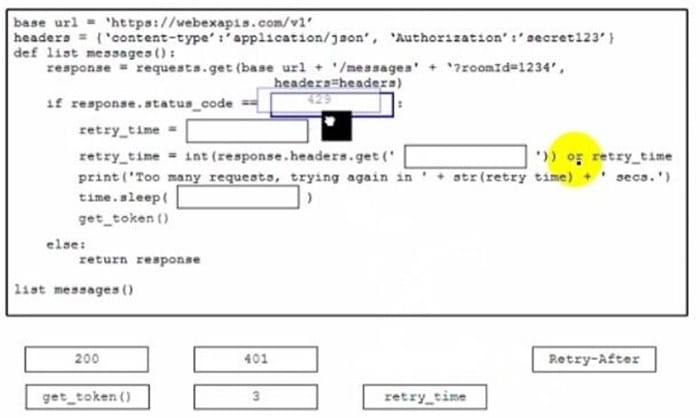
Correct Answer:
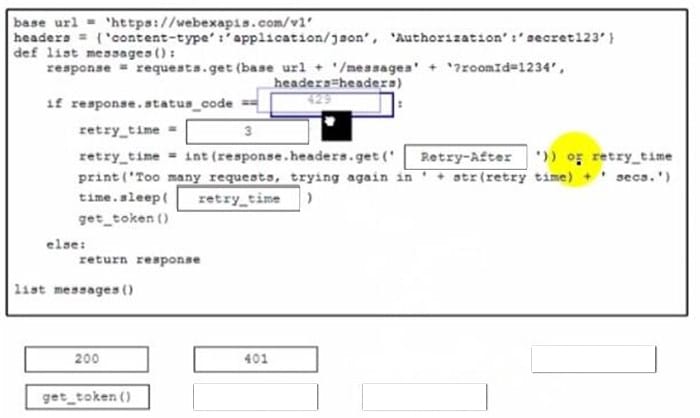
- Place
429afterresponse.status_code ==to check for the rate limit status code. - Place
'Retry-After'insideresponse.headers.get()to extract the retry delay from the response headers. - Place
retry_timeinsidetime.sleep()to pause execution for the specified duration. - Place
list_messages()in thereturnstatement within theifblock to recursively retry the API call after sleeping.
Explanation:
This question tests understanding of implementing retry logic for API rate limiting (HTTP 429 status).
The code handles the “Too Many Requests” error by parsing the Retry-After header for the wait time, sleeping accordingly, and recursively calling the function to retry without disrupting the overall flow.
Using get_token() would be incorrect as it calls a separate unrelated function; status codes like 200 or 401 and literal values like 3 are not relevant here.
Question 2 (single choice)
A local data center deployment using Cisco NX-OS switches is scaling and requires automatic configuration at scale. Configuration management must be set up for a Cisco NX-OS switch by using Ansible. The Ansible control server is currently located on a different subnet than the switch. The solution has these requirements:
- The transport protocol used must be encrypted
- The connections must originate from a server in the same local network
- Enable mode must be supported
Which connectivity method must be used?
A. SSH through a bastion host and ansible_become method for privilege escalation.
B. HTTPS through a repository and ansible_become method for privilege escalation
C. XML-RPC through a web proxy.
D. HTTP through a web proxy.
Correct Answer: A
Explanation:
This question tests the understanding of secure, subnet-crossing connectivity for Ansible automation on Cisco NX-OS switches.
Option A uses SSH for encryption, a bastion host in the local network to satisfy origination requirements, and ansible_become to handle enable mode escalation without business disruption.
Options B and D fail on encryption or proper subnet handling, while C uses an unsupported or unencrypted protocol for NX-OS via Ansible.
Question 3 (Multiple choice)
Refer to the exhibit.
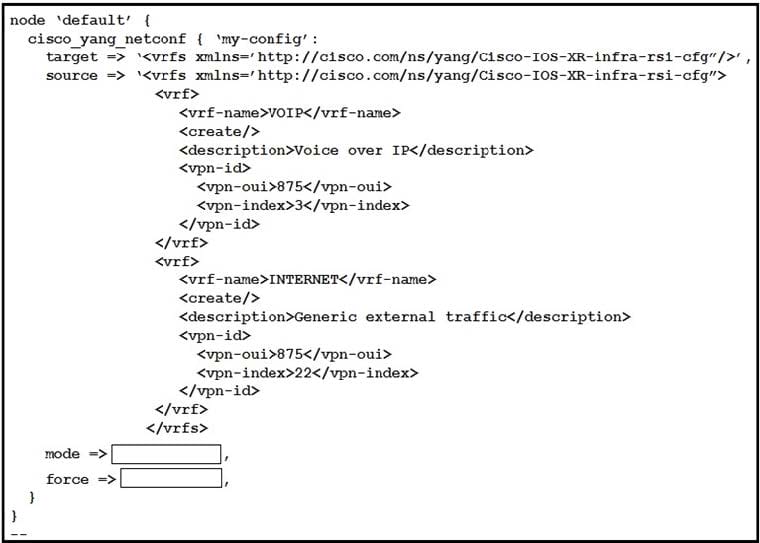
This script uses ciscoyang to configure two VRF instances on a Cisco IOS-XR device using the Yang NETCONF type.
Which two words are required to complete the script? (Choose two.)
A. ensure
B. commit
C. false
D. replace
E. none
Correct Answer: C D
Explanation:
This question tests knowledge of ciscoyang module parameters in Ansible for Cisco IOS-XR configuration. The ‘mode’ parameter should be set to ‘replace’ to overwrite existing VRF configurations atomically, and ‘force’ to ‘false’ to avoid automatic commits that could disrupt running services, aligning with best practices for NETCONF-based automation.
Question 4 (Multiple choice)
What are two steps in the OAuth2 protocol flow? (Choose two.)
A. The user is authenticated by the authorization server and granted an access token.
B. The user’s original credentials are validated by the resource server and authorization is granted.
C. The user indirectly requests authorization through the authorization server.
D. The user requests an access token by authentication and authorization grant presentation.
E. The user requests the protected resource from the resource server using the original credentials.
Correct Answer: AE
Explanation:
This question examines the candidate’s understanding of the core steps in the OAuth 2.0 authorization protocol flow.
In the abstract OAuth 2.0 flow, the user (resource owner) is authenticated by the authorization server, which issues an authorization grant (such as an access token or code) to the client on the user’s behalf (A). The user then accesses the protected resource via the client, which presents the token to the resource server, though the flow emphasizes delegation without direct credential use (E).
Options B, C, and D misrepresent the roles of the resource server, indirect requests, and token exchange, which are handled by the client rather than the user directly.
Reference: https://www.digitalocean.com/community/tutorials/an-introduction-to-oauth-2
Question 5 (DRAG DROP)
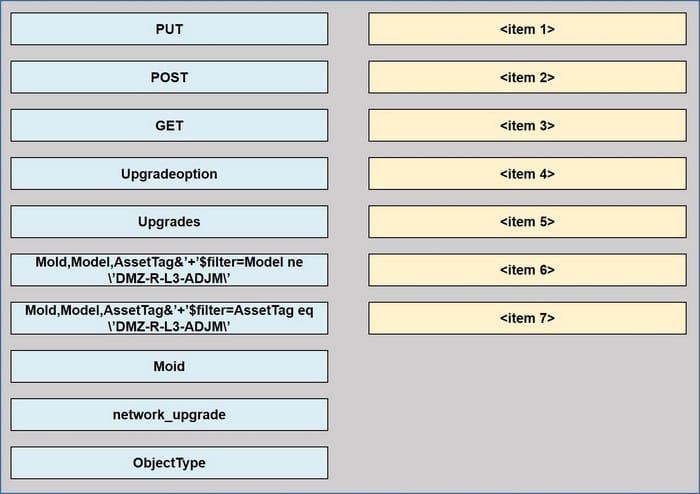
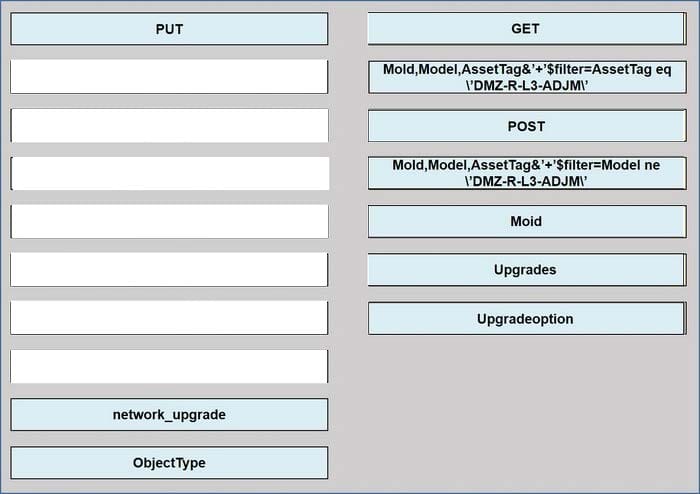
Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question. The script uses the Cisco Intersight REST API. Drag and drop the code snippets from the left onto the item numbers on
the right to match the missing sections in the Python script to update the firmware on specific Cisco Intersight USC rack server.DMZ_R-L3-ADJM.
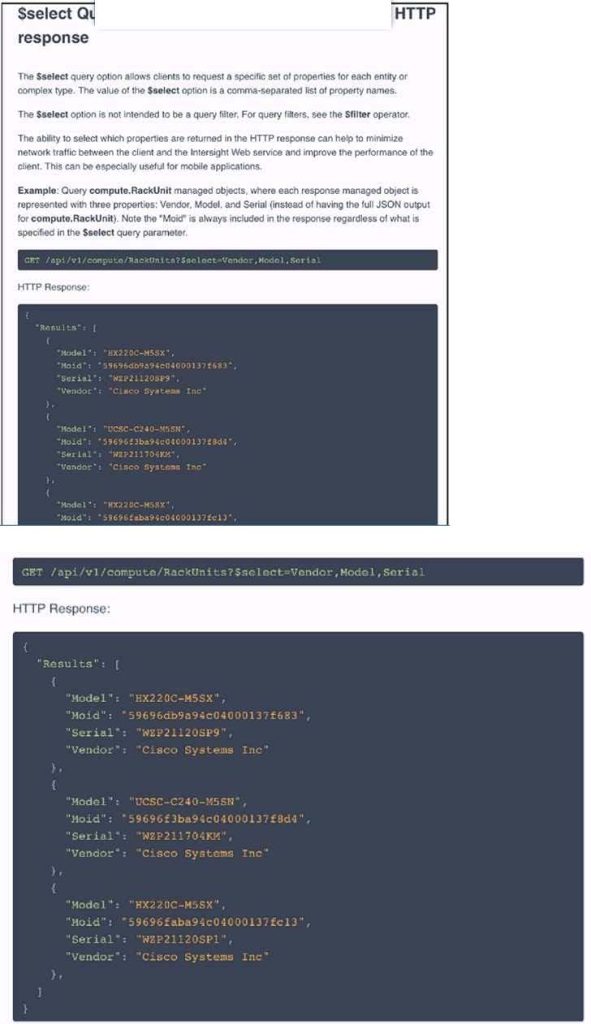
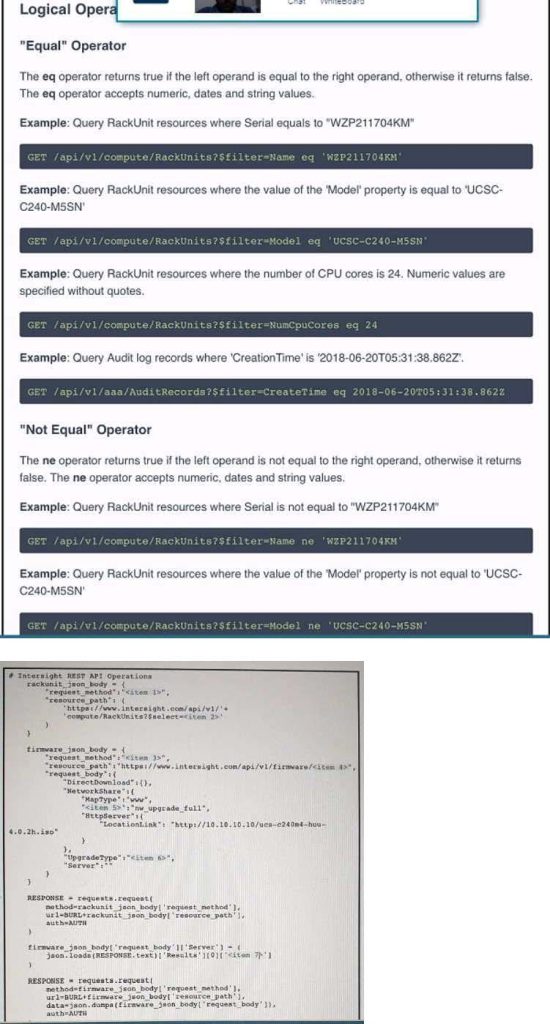
Not all code snippets are used.
Select and Place:
Correct Answer:
Question 6 (single choice)
Refer to the exhibit. The cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file “@token_data” that cURL is handling?
curl --insecure -H "Accept: application/json" -H "Content-Type: application/json" -d @token_data https://ast0072-pod.cisco.com:3333/api/fdm/latest/fdm/tokenA. This file is a container to log possible error responses in the request.
B. This file is given as input to store the access token received from FDM.
C. This file is used to send authentication related headers.
D. This file contains raw data that is needed for token authentication.
Correct Answer: D
Explanation:
This question tests the candidate’s knowledge of cURL syntax and OAuth token request mechanics in API interactions.
The -d @filename option in cURL specifies that the POST request body data is read from the named file, which here contains the necessary payload (e.g., client credentials like client_id and client_secret in JSON format) required to authenticate and obtain the access token from the FDM endpoint.
Option A is incorrect as error logging is not handled by -d; B misinterprets the direction (input vs. output—output would use -o); and C is wrong since headers are set via -H flags.
Question 7 (DRAG DROP)
Drag and drop the code from the bottom onto the box where the code is missing to enable an SSID by using the Cisco Meraki Dashboard API. Not all options are used.
Select and Place:
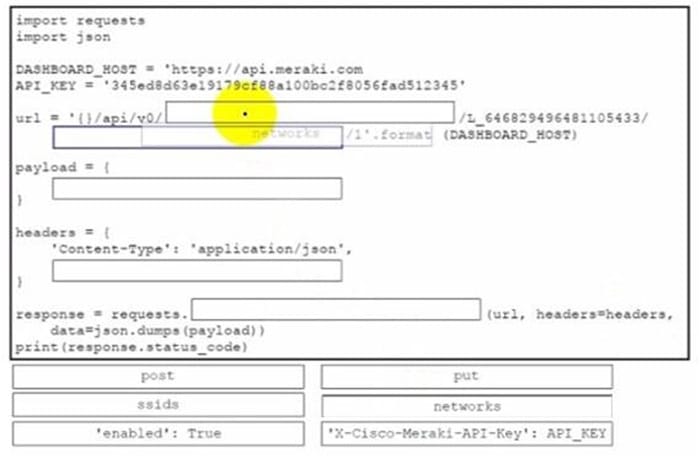
import requests
import json
API_KEY = "345ed6d3e17f9f68100bcf8056fad519"
url = "/api/v0/networks/{network_id}/ssids/{number}"
payload = {
"enabled": True
}
headers = {
"Content-Type": "application/json",
"X-Cisco-Meraki-API-Key": API_KEY
}
response = requests.put(url, headers=headers,
data=json.dumps(payload))
print(response.status_code)Correct Answer:
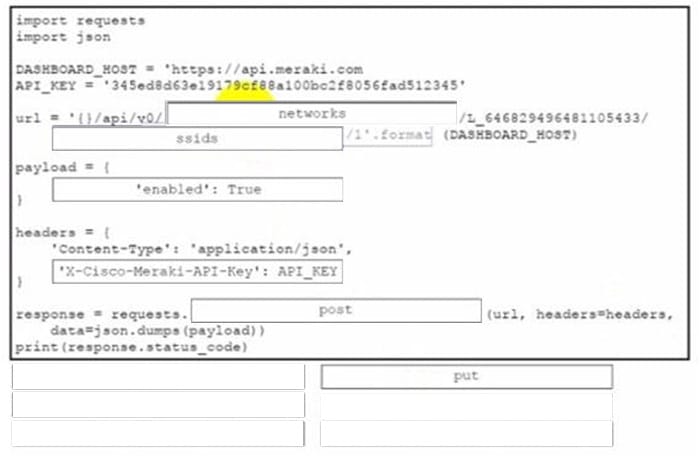
- Method: put
- Payload: {“enabled”: True}
- Headers: “X-Cisco-Meraki-API-Key”: API_KEY
Explanation:
This question assesses the candidate’s familiarity with the Cisco Meraki Dashboard API for updating wireless SSID configurations.
To enable an SSID, a PUT request must be made to the /networks/{networkId}/ssids/{number} endpoint with a JSON payload setting “enabled”: true, and the required authentication header “X-Cisco-Meraki-API-Key” must be included. Using POST would be incorrect for updates, and other options like SSL configurations or status fields are irrelevant for this operation.
Question 8 (Multiple choice)
Refer to the exhibit.
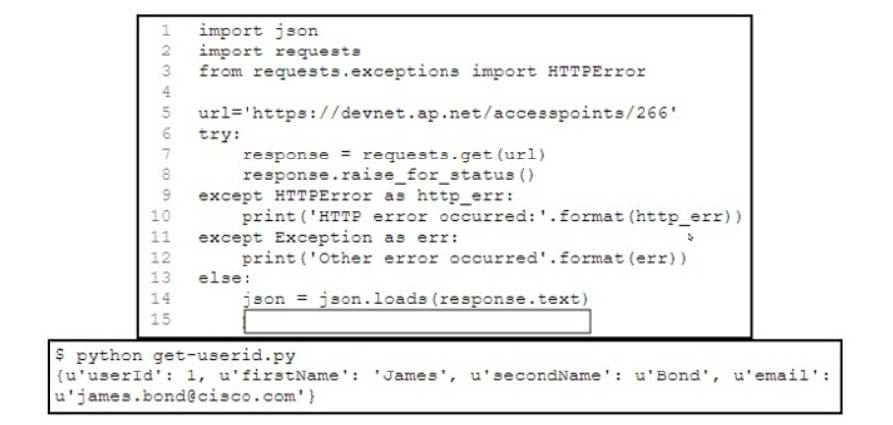
import json
import requests
from requests.exceptions import HTTPError
url='https://devnet.apic.net/accesspoints/266'
try:
response = requests.get(url)
response.raise_for_status()
except HTTPError as http_err:
print('HTTP error occurred: '.format(http_err))
except Exception as err:
print('Other error occurred: '.format(err))
else:
json = json.loads(response.text)
[blank]A developer has created a Python script that retrieves information about the deployment of Cisco wireless access points using REST API.
Which two code snippets must be added to the blank in the code to print the value of the userid key instead of printing the full JSON response? (Choose two.)
A. print json[0] [userId]
B. print json[‘userId’]
C. print json[1] [‘userId’]
D.
for key, value in json.items():
if key == 'userId':
print( '{}'.format(value) )E.
for key, value in json.dumps(response.text):
if key in 'userId':
print valueCorrect Answer: BD
Explanation:
This question evaluates the candidate’s proficiency in Python JSON handling and dictionary access patterns for API response parsing.
The response is a JSON object loaded into a Python dictionary (not a list), so direct key access via json[‘userId’] (B) retrieves and prints the value (1).
Iterating over json.items() to conditionally print the matching key’s value (D) also achieves this.
Option A assumes a list structure with index 0, which fails as it is a dict; C uses an invalid index 1; and E incorrectly iterates over a string (from json.dumps()) and uses flawed conditional logic (if key in ‘userId’ treats the key as a substring check).
Question 9 (single choice)
Which type of file is created from issued intermediate, root, and primary certificates for SSL installation on a server?
A. DER
B. CSR
C. PEM
D. CRT
Correct Answer: C
Explanation:
This question tests the candidate’s knowledge of common SSL/TLS certificate file formats and their use cases in server installations.
PEM (Privacy Enhanced Mail) format is a text-based (Base64-encoded) container that allows concatenation of multiple certificates—such as the primary (server) certificate, intermediate certificates, and root CA certificate—into a single.
pem file for easy import and chain validation during SSL setup. DER is a binary format unsuitable for concatenation without tools; CSR (Certificate Signing Request) is used to request certificates, not store issued ones; and CRT is a generic extension that can hold PEM or DER content but does not inherently support bundled chains as flexibly as PEM.
Question 10 (single choice)
Which security approach should be used for developing a REST API?
A. Use custom security relevant HTTP response codes
B. Utilise TLS for end to end encryption
C. Add an API key to each URL string
D. Utilize CORS headers
Correct Answer: B
Explanation:
This question assesses the candidate’s understanding of foundational security principles for REST APIs, emphasizing protection of data in transit.
TLS (Transport Layer Security) provides end-to-end encryption, ensuring confidentiality, integrity, and authenticity of communications between clients and the API server, which is a mandatory best practice per standards like OWASP API Security guidelines.
Option A is incorrect as custom HTTP codes can lead to interoperability issues without enhancing security; C exposes API keys in logs or referer headers, violating least privilege principles; and D addresses browser-specific cross-origin restrictions but does not secure the API against broader threats like eavesdropping or tampering.
Question 11 (single choice)
User report that they can no longer process transactions with the online ordering application, and the logging dashboard is displaying these messages.
Fri Jan 10 19:37:31.123 EST 2020 [FRONTEND] INFO: Incoming request to add item to cart from user 45834534858
Fri Jan 10 19:37:31 247 EST 2020 [BACKEND] INFO: Attempting to add item to cart
Fri Jan 10 19:37:31 250 EST 2020 [BACKEND] ERROR: Failed to add item: MYSQLDB ERROR: Connection refusedWhat is causing the problem seen in these log messages?
A. The database server container has crashed. B. The backend process is overwhelmed with too many transactions. C. The backend is not authorized to commit to the database. D. The user is not authorized to add the item to their cart.
Correct Answer: A
Explanation:
This question tests the candidate’s ability to interpret application logs for troubleshooting database connectivity issues in a microservices architecture.
The “Connection refused” error from the MySQL driver indicates that the backend cannot establish a TCP connection to the database server, commonly due to the server being unavailable (e.g., crashed container or stopped service).
Option B lacks evidence of high load (no queue or timeout indicators); C would typically show an authentication/permissions error like “Access denied”; and D would fail earlier in the request flow, before the backend attempts the database operation.
Question 12 (single choice)
Which command is used to enable application hosting on a Cisco IOS XE device?
A. app-hosting
B. application-hosting
C. iox
D. iox-service
Correct Answer: A
Explanation:
This question evaluates the candidate’s knowledge of Cisco IOS XE programmability features for containerized application hosting.
The app-hosting command in privileged EXEC mode activates the Application Hosting infrastructure, enabling the deployment and management of Linux-based applications in isolated containers via IOx.
Option B is a non-existent variant; C refers to the IOx framework itself but is not the enabling command; and D is used for managing specific IOx services, not enabling hosting overall.
Question 13 (single choice)
Refer to the exhibit.
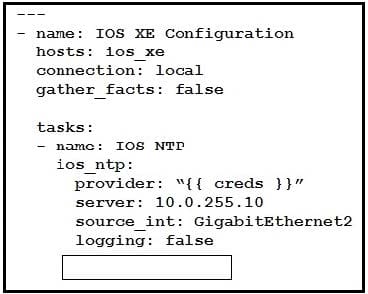
Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
A. state: present
B. state: True
C. config: present
D. config: True
Correct Answer: A
Explanation:
ios_ntp : Manages core NTP configuration state : Manage the state of the resource Choices : present | absent Example: # Set new NTP server and source interface
-ios_ntp: server: 10.0.255.10 source_int: Loopback0 logging: false state: present
https://docs.ansible.com/ansible/latest/modules/ios_ntp_module.html
Question 14 (DRAG DROP)
Drag and drop the code from the bottom onto the box where the code is missing to retrieve a summary of physical compute resources. The collected information about the compute resources will be presented in a dashboard to be developed for device monitoring purposes. Not all snippets are used.
Select and Place:
import requests
import json
BASE_URL = "https://intersight.com/api/v1"
url = [f"{BASE_URL}/compute/PhysicalSummaries"]
payload = {
}
headers = {
"Accept": "application/json",
"Authorization": [f"Signature (httpsig)"],
"Digest": "{(computed-digest)}",
"Date": "{(current-date)}"
}
response = requests.request(
["GET"],
url,
headers=headers,
data=json.dumps(payload),
)
print(response.text.encode('utf-8'))Correct Answer:
- URL: f”{BASE_URL}/compute/PhysicalSummaries”
- Method: “GET”
- Authorization: f”Signature (httpsig)”
Explanation:
This question evaluates the candidate’s understanding of Cisco Intersight REST API interactions for querying compute resources using Python’s requests library.
The /compute/PhysicalSummaries endpoint with a GET method retrieves a list of physical server summaries, ideal for monitoring dashboards.
Authentication employs HTTP Signature scheme (via API keys), requiring the Authorization header with a computed signature, alongside Digest (for request body hash, empty for GET) and Date headers for integrity and freshness.
The /compute/ListPhysical endpoint and Bearer token are distractors—Bearer is for OAuth2 flows, not primary API key auth, and ListPhysical targets a different resource set.
Question 15 (DRAG DROP)
Drag and drop the code from the bottom onto the box where the code is missing to delete a host object by using the Cisco Firepower Device Manager API. Not all options are used.
Select and Place:
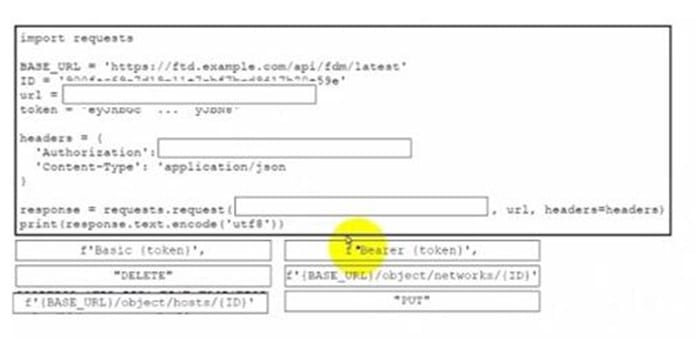
import requests
BASE_URL = "https://fdm.example.com/api/fdm/latest"
ID = "uuid...uuid"
url = f"{BASE_URL}/objects/hosts/{ID}"
token = "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9..."
headers = {
"Authorization": [blank],
"Content-Type": "application/json"
}
response = requests.request(
[method],
url,
headers=headers
)
print(response.text.encode('utf-8'))Correct Answer:
- Authorization: f”Bearer {token}”
- Method: “DELETE”
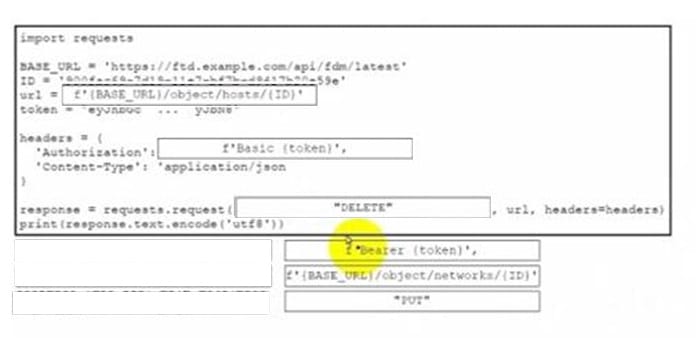
Explanation:
This question evaluates the candidate’s understanding of REST API methods and authentication for resource management in the Cisco Firepower Device Manager (FDM).
Deleting a host object requires a DELETE request to the /objects/hosts/{id} endpoint, secured with a Bearer token in the Authorization header obtained from prior OAuth authentication.
Basic authentication is used only for token issuance, not deletions; POST is for creating objects; and the networks endpoint applies to different object types like address groups.
…
How to Use PDF and VCE Formats
Understanding how to leverage PDF and VCE formats can significantly enhance your preparation for the Cisco 350-901 DEVCOR exam. These formats are designed for flexibility and efficiency, allowing you to study on the go or simulate real exam conditions.
PDF Format Benefits and Usage:
- Portability and Readability: PDF files are ideal for offline reading on any device, such as laptops, tablets, or smartphones. Use them to review detailed explanations, diagrams, and study notes at your own pace.
- How to Use: Simply download the PDF and open it with a free reader like Adobe Acrobat or a browser. Highlight key sections, take notes in the margins, or print pages for traditional studying.
- Free Sample: Get started with our complimentary PDF sample containing 10-15 essential questions and answers: [ https://drive.google.com/file/d/1T6IAexTvGJNRl65Lo3NC0hcSK4Dsky3z/view?usp=sharing ].
VCE Format Benefits and Usage:
- Exam Simulation: VCE (Virtual Exam Converter) files mimic the actual Cisco exam environment, including timed questions, multiple-choice, drag-and-drop, and code-based interactions. This helps build stamina and identify weak areas.
- How to Use: Install a VCE-compatible player like Exam Simulator or VCE Exam Simulator (free versions available). Import the VCE file and run practice sessions. Track your scores and review incorrect answers for deeper learning.
- Premium Access: For the full 350-901 VCE dump with 463+ updated questions and 365-day free updates, visit [ https://www.leads4pass.com/350-901.html ] and subscribe for instant access.
By combining both formats, you’ll gain a comprehensive edge – PDFs for foundational knowledge and VCE for practical testing. Start practicing today to ace your certification!
Conclusion
In summary, this updated guide equips you with live-updated Cisco 350-901 DEVCOR dumps in PDF and VCE formats, helping you save time and money while preparing for the 2025 exam – and staying ahead of the 2026 v2.0 changes. By leveraging these resources, you’ll build a solid foundation in software development, APIs, and automation to ace your Cisco Certified DevNet Professional certification.

